Toll Fraud is Expensive Nightmare That’s 100% Preventable
[ad_1]
Toll fraud occurs when scammers illegally entry an organization’s telephone system to name high-cost, premium-rate numbers. It’s a severe difficulty in telecommunications, costing the trade a staggering $39 billion yearly.
In 2021, the common price per incident was $40,000 for toll fraud involving distant staff. One telecom firm specifically even recognized and halted the fraudulent calls in beneath an hour—but the scammers nonetheless collected expenses of $2,133.58.
Having to pay the charges related to toll fraud will be devastating to an organization, particularly for smaller companies. Thus, taking the time to be taught in regards to the measures you possibly can take to stop it’s time properly spent.

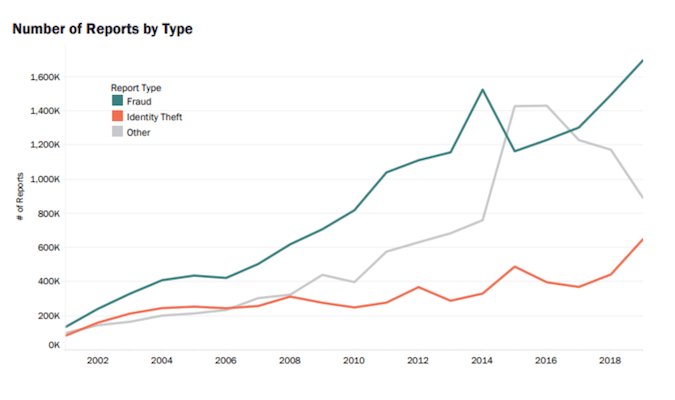
Fashionable Toll Fraud Is On Each Channel
Remember the fact that toll fraud shouldn’t be restricted to voice calls, because it extends throughout varied platforms, together with VoIP and SMS.
Widespread Varieties of Toll Fraud
Every of the various types of toll fraud comes with distinctive strategies and impacts. The most important forms of toll fraud you need to be conscious of to guard what you are promoting are as follows:
- Wangiri Fraud: “Wangiri” means “one and minimize” in Japanese. On this rip-off, the fraudster calls and hangs up after one ring, prompting the recipient to name again a pricey quantity they management.
- Modified-Wangiri Assault: It is a twist on Wangiri fraud by which scammers name an organization’s system from a high-cost quantity and request a callback. When the corporate calls again, it incurs vital expenses.
- Interconnect Bypass Fraud: Also referred to as SIM field fraud, this includes utilizing gadgets to reroute worldwide calls at decrease prices whereas charging the caller regular charges.
- PBX Hacking: Hackers entry an organization’s non-public telephone community (PBX) and use it to make calls to premium-rate numbers.
- Account Takeover: If scammers receive login particulars for telecom accounts, they’ll use them to make unauthorized calls or transactions, resulting in expenses for the account house owners.
- Worldwide Income Share Fraud (IRSF): That is when scammers make faux calls to premium numbers beneath revenue-sharing agreements, mixing them with actual calls to keep away from detection and inflicting losses for each telecoms and their clients.
- VoIP Fraud: Some hackers will goal VoIP gadgets with weak safety, utilizing them to make costly worldwide calls and promote entry to those routes at decrease charges.
- SMS Pumping: This includes sending a big quantity of SMS messages to premium-rate numbers (managed by the identical scammers), exploiting cellular community operators to generate illicit income.
- Voice Verification Code Spamming: That is when fraudsters use voice verification in 2FA techniques, launching scripted assaults to create many calls—usually to pricey worldwide numbers.
- SMS Verification Code Spamming: Just like voice spamming, this technique makes use of faux verification texts despatched en masse. It targets high-cost SMS locations to generate income.
6 Easy Techniques for Toll Fraud Prevention
Protecting what you are promoting secure from toll fraud, particularly in VoIP techniques, is critically essential. Keep in mind these six tricks to keep one step forward:
1. Don’t Go away Ports Open
Open ports are needed for digital techniques to perform, particularly VoIP. In the meantime, Session Initiation Protocol (SIP) ports, similar to 5060, have to be open to allow VoIP communications—and this poses dangers.
For instance, port scanning, which is when hackers search for open ports to use, can result in fast assaults. Unprotected ports will be hit with spam or extra extreme assaults like toll fraud or knowledge breaches.
To open ports extra securely, bear in mind to make use of firewalls and VPNs.
Utilizing multi-factor authentication (MFA) is one other good thought to boost safety additional, as is working common audits in your community to determine which ports are open. You possibly can accomplish this through the use of community instruments to detect and shut ports that aren’t wanted whereas additionally guaranteeing that important ports for providers like e mail servers stay open and safe.
To find out which ports are open and be certain that solely licensed visitors is allowed, observe these steps:
- Conduct a Port Scan: Use community scanning instruments to carry out a port scan. This may determine all open ports in your community. Instruments like Nmap can present an in depth overview of your community’s open ports.
- Analyze and Evaluation: Analyze the scan outcomes to know why every port is open. Decide if the open ports are needed in your operations or in the event that they pose a safety danger.
- Implement Entry Controls: For needed open ports, implement strict entry controls. This contains configuring firewall guidelines to permit solely trusted IP addresses and establishing VPNs for safe distant entry.
- Common Monitoring: Constantly monitor your community’s visitors to detect any uncommon exercise. Organising intrusion detection techniques might help determine potential unauthorized entry makes an attempt.
2. Common Monitoring and Patching
Outdated software program is answerable for 34% of safety breaches, and patch administration is crucial to deal with this concern.
Patch administration includes constantly monitoring your community for brand new vulnerabilities and deploying the suitable updates for them. Checking for brand new patches mechanically is a wonderful means to make sure well timed updates and scale back the danger of human error.
It’s additionally essential to prioritize vulnerabilities. A scoring system just like the Widespread Vulnerability Scoring System (CVSS) charges the severity of vulnerabilities, which helps you focus your assets on probably the most vital points. Taking a risk-based method (underpinned by common monitoring) will be certain that any high-risk vulnerabilities are addressed promptly, lowering your organization’s danger for exploitation by cyber attackers.
3. Robust Account Safety
There are a number of methods you possibly can improve your account safety to guard towards the danger of toll fraud.
- Create Robust Passwords: Password administration is essential. Use distinctive, advanced passwords for every platform and change default passwords with sturdy, particular person ones. Shortly change your passwords if there’s ever a breach in your service supplier’s safety, particularly if you happen to’ve used the identical password elsewhere—which you shouldn’t have executed within the first place, ya goof.
- Use Two-Issue Authentication (2FA): This provides an additional layer of safety to your accounts by requiring two forms of identification, similar to a code despatched to your telephone or a biometric scan, making it tougher for unauthorized entry even when a password is compromised.
- Preserve communication safety: Be cautious with communication and knowledge storage. Keep away from sending delicate info like passwords or SIP account particulars by way of unencrypted e mail. Additionally, chorus from storing passwords in simply accessible locations.
- Use role-based entry: Outline consumer permissions and entry ranges for every staff member, guaranteeing they solely have entry to software program and knowledge wanted for his or her particular roles.
4. Geo Permissions and Price Limits
Geo permissions management verification visitors to vacation spot international locations for SMS and voice channels, lowering the danger of exploitation by SMS pumping and toll fraud. By setting these permissions, you possibly can prohibit visitors from international locations the place what you are promoting doesn’t function, in addition to monitor visitors to detect and block fraudulent actions.
Alongside geo permissions, implementing charge limits is essential. Price limiting includes controlling the variety of calls or messages despatched to a selected vacation spot inside a given timeframe. This may be significantly efficient in mitigating toll fraud dangers.
For instance, setting limits on the variety of calls allowed per minute or per day to high-risk international locations can forestall huge monetary losses as a consequence of toll fraud. By combining geo permissions with strategic charge limits, you possibly can successfully safe your telecommunication visitors towards fraudulent actions.
5. Community and PBX Safety
Past the fundamental account safety measures of utilizing sturdy passwords and 2FA, further community and PBX safety measures embrace:
- Configuring PBX Audits: Operating PBX audits might help determine and disable pointless providers or options. This proactive step helps shut potential safety gaps that would result in many situations of toll fraud.
- Implementing Community Segmentation: Section your community to create separate zones for voice and knowledge visitors. This separation enhances safety and restricts entry to the PBX system in case of a breach, lowering the general danger of toll fraud.
- Utilizing VoIP-Particular Firewalls: Make use of firewalls tailor-made for VoIP visitors to safeguard SIP protocols. These specialised firewalls provide stronger safety towards assaults, mitigating the danger of unauthorized calls that may incur vital prices for what you are promoting.
- Putting in Session Border Controllers (SBCs): SBCs assist forestall unauthorized entry to your VoIP community, thus defending it towards toll fraud and the misuse of your VoIP system by exterior threats.
6. Worker Coaching and Insurance policies
Efficient worker coaching and insurance policies are very important in stopping toll fraud and guaranteeing community safety. You’ll want to have complete coaching packages that cowl the basics of cybersecurity, particular dangers associated to toll fraud, and the significance of sustaining sturdy account safety.
Frequently scheduled coaching classes, together with onboarding for brand new staff and periodic refreshers for present workers, be certain that everyone seems to be updated with the most recent safety practices and protocols. These classes ought to embrace sensible situations and real-world examples to assist staff perceive the significance of their particular person roles in safeguarding the corporate’s telecommunications techniques.
Along with offering coaching, it’s additionally essential to have well-defined insurance policies that define pointers for password administration, procedures for reporting suspicious actions, and protocols for responding to safety breaches. Keep in mind to maintain your insurance policies clear, accessible, and constantly enforced.
[ad_2]
Source_link







