With out SIP Safety, Name Knowledge Is An Open Ebook to Hackers
[ad_1]
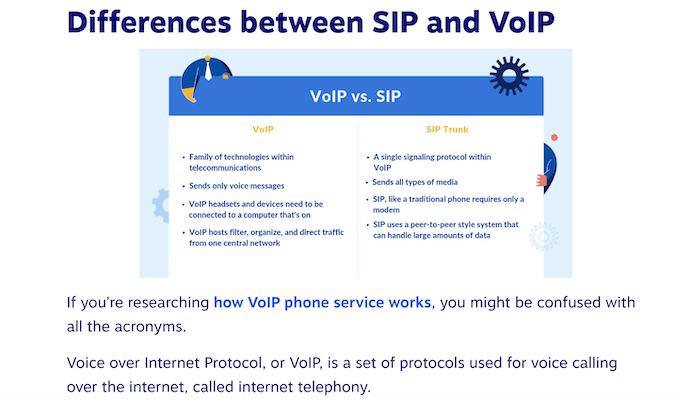
Session Initiation Protocol (SIP) is the particular sequence of steps required to start or terminate the transmission of voice or video knowledge between two or extra units on a cloud-based community. Over time, nearly all of enterprise house owners are shifting on from the older, copper wire-based telecommunications techniques in favor of newer know-how resembling Voice over Web Protocol (VoIP), which as a substitute allows the identical dependable communication over the web.
SIP is an integral piece of VoIP know-how, because it offers enterprise house owners and name middle service suppliers the power to supply an abundance of performance at a fraction of conventional landline prices. Thus, gone are the times whenever you needed to pay a telephone firm a month-to-month charge for tens and even tons of of bodily traces held for what you are promoting and workers to make use of. Now, with the assistance of SIP, most of the high VoIP distributors (resembling RingCentral or Nextiva) can set up a digital line everytime you want it, charging just for the precise time spent on every line.
Altogether, SIP know-how presents community customers with a quick and dependable technique of transmitting voice and video knowledge between smartphones, computer systems, and even desk telephones. Nevertheless, this open line will be exploited by hackers in the event you aren’t cautious.

Why SIP Safety is a Should
SIP was not initially developed with private safety in thoughts. In reality, it’s a text-based protocol that appears quite a bit just like the common HyperText Markup Language (HTML) we see on web sites and in emails. Because of this, the entire info contained in every SIP transmission—together with particular system info, knowledge varieties, and community particulars—can simply be intercepted and browse. All it takes is one hacker with the essential expertise to eavesdrop in your web community.
Should you’re questioning why a hacker would possibly hassle focusing on enterprise IP networks, the reply lies each within the knowledge you’re transmitting and within the capabilities of your system. In case your name, textual content, or voice knowledge contains login credentials or different delicate info, it might be helpful for hacking private or shopper accounts.
Alternatively, a hacker can also wish to seize the unique use of your IP port, basically taking your telephone line hostage. If profitable, they’ll then name tons of of premium price numbers to costly worldwide locations. This rip-off is called toll fraud, and it earns hackers billions per yr from complicit service suppliers, typically costing enterprise house owners extra in damages than bank card fraud.
From the inception of SIP know-how, opportunistic criminals have developed a wide range of frequent assault maneuvers that at the moment are extensively identified all through the IT world. These embrace:
- Man-in-the-Center Assaults: An unsecured Wi-Fi connection will be intercepted, rerouting calls to a different server the place your system turns into weak to dangerous malware and viruses
- SIP Register Flood: When your VoIP community is overwhelmed by faux connection requests to make use of up your web bandwidth
- Denial of Service (DoS): Your whole community is held hostage, barring you from entry with out making cost
- Name Tampering: A noise packet will be inserted into your knowledge stream, ruining name high quality
- Vishing: Much like textual content or electronic mail phishing however on a VoIP community, delicate info is solicited via a URL hyperlink or telephone quantity
- Name Hijacking: Your Wi-Fi hotspot will be accessed to steal info or siphon web service
- ID Spoofing: A hacker mimics a telephone quantity from a trusted supply to achieve entry to your knowledge
SIP Safety: SIPS and SRTP
As soon as SIP establishes a connection between or amongst system customers, Actual time Switch Protocol (RTP) is used to transmit voice or video knowledge, with SIP terminating the decision on the finish. As a result of how HTML is utilized in each protocols, they’re extremely vulnerable to interception and corruption. To fight this, IT specialists developed SIP Safe (SIPS) and Safe RTP (SRTP) to guard every side of your calls—together with each the connection particulars and the decision knowledge itself.
SIPS opens a digital name line utilizing Transport Layer Safety, which is similar protocol used to encrypt on-line funds via HTTPS web sites. On this case, it establishes a safe channel and authenticates customers whereas encrypting their personal particulars and preserving the integrity of the information.
Likewise, SRTP does the identical factor in the course of the knowledge transmission in a handshake-like course of between person ports. Every name generates a singular algorithm key that encrypts and decrypts knowledge as it’s transmitted and obtained at its vacation spot port. The result’s a safe connection from the time the decision is initiated to the second of termination.
Though each protocols are the present gold requirements for shielding digital communications networks from cyberattacks, they’re solely appropriate with units that help SIPS and SRTP encryption. Nonetheless, specialists agree that such privateness instruments must be employed when working on a Native Space Community (LAN) or cloud-based community the place assaults are seemingly.
SIP Safety Greatest Practices
It’s as much as your particular VoIP supplier whether or not or not SIPS and SRTP protocols are engaged in all knowledge transmissions. You possibly can simply discover out by asking your customer support consultant if the service makes use of end-to-end encryption and whether or not or not calls ever transmit knowledge over the Public Switched Phone Community (PSTN).
Along with the safety measures taken by your VoIP host, there are a selection of steps you may take to additional safeguard what you are promoting communications, resembling:
- Imposing a Sturdy Password Coverage: Even with a hosted telephone system, hackers can use scanners to find weak accounts and acquire entry. Advise workers on creating robust passwords that use higher and lowercase letters, symbols, and numbers. Be sure they keep away from storing this delicate info in a web-accessible doc or equally discoverable location. Use multi-factor authentication when attainable, including a second step to confirm crew member identities earlier than granting system entry.
- Solely Permitting SIP Site visitors To and From Your ITSP: Simply as you wouldn’t reply a name from an unknown quantity on a non-public line, be certain all SIP communication is routed via your Web Phone Service Supplier (ITSP). Arrange your system to permit transmissions solely by way of acknowledged IP addresses and SIP ports. In any other case, you run the chance of getting your port hijacked and used to make unauthorized connections.
- Repeatedly Updating Software program and Firmware: Be sure that all applications and tools are updated with the most recent, most superior safe encryption know-how. Any system used for business-related communication ought to help SIPS and SRTP for full name safety. An outdated system can create vulnerabilities that cyberattackers wish to exploit.
- Establishing a Digital Non-public Community (VPN): An encrypted VPN creates a safe connection between person units and your shared enterprise community. Authenticated distant entry additionally permits crew members to interact this community even when they’re working offsite. All knowledge transmitted over your VPN is encrypted to forestall hackers from decoding any intercepted info. Messages are usually recognized as being from an authenticated sender to forestall phishing and different infiltration makes an attempt.
- Educating Your Group: Consider each crew member as a hyperlink within the protecting chain that retains your community safe. Be sure they’re up to date on the most recent greatest practices, resembling setting robust passwords and recognizing any potential makes an attempt to achieve unauthorized system entry. Any company-owned {hardware}, together with laptops and telephones, must be upgraded usually and up to date with probably the most superior safety software program.
- Proscribing and Evaluating Calls: Many VoIP platforms embrace a way of blocking costly worldwide telephone numbers in order that hackers received’t be capable of run up your invoice with toll fraud even when they acquire entry. Such platforms usually empower enterprise house owners to keep up name logs of each incoming or outbound communication on their community. You possibly can evaluate these logs regularly and call your VoIP supplier in the event you discover any unauthorized exercise.
- Distant Gadget Administration: Outfit your work-related units with software program that has exercise monitoring capabilities and distant system wiping from one central location, resembling your principal workplace. That is particularly vital for workers who work remotely or journey steadily and could also be uncovered to numerous community or system vulnerabilities.
All in all, VoIP-related capabilities like SIP assist enterprise house owners maximize their telecommunications efficiency at a way more aggressive value level than conventional landline networks.
On the identical time, organizations that embrace these superior technological options might unknowingly expose themselves to unexpected losses by the hands of scammers, so it’s vital to take correct precautions.
Fortuitously, a bit of additional effort and perception can hold you one step forward of the hackers, defending the safety of your name knowledge so that you get pleasure from the advantages of VoIP, stress-free.
[ad_2]
Source_link







